
What is a Penetration Test?
Penetration testing, which can also be called pen testing or ethical hacking, involves an authorised attempt to gain unauthorised access to a computer system, application, or data. Often a penetration test will involve replicating strategies that are utilised by hackers. This helps to identify security vulnerabilities that can then be resolved before a malicious attacker has the opportunity to exploit them.
Why you need a Pen Test
With the help of a pen test, you can identify the origins of cybersecurity weaknesses – and identify possible weaknesses that would expose your business to future attacks. As a business we aim to provide preventative strategies as opposed to cures, continually delivering robust and up-to-date solutions. Penetration testing is a fundamental element in us providing our clients with prudent and protective IT strategy.


What type of business' use Pen Test
No business is too small to be attacked by cyber-criminals. Security flaws exist in software, hardware, and configurations irrespective of the size of the organisation. Additionally, there are now regulatory requirements for penetration tests to be conducted across businesses of all statures.
“Everyone from the management team to the engineers on the front line are friendly and efficient. I value that they can all translate IT to plain English so I don't feel like I need to be IT literate! When working with Fitzrovia, you feel like you are working in partnership rather than with a supplier of a service.”
Preeya G
End-User Benefits of a Penetration Test
Employees personal data is safe
Your employees will have peace of mind knowing that their company is actively ensuring that their personal details are safe.
Avoid being in the public eye for breaches
No one wants to explain to friends and family how and why their employer was breached.
Minimise department downtime
The chances of work and projects being stalled are minimised for end users who will not have to wait while systems are restored.
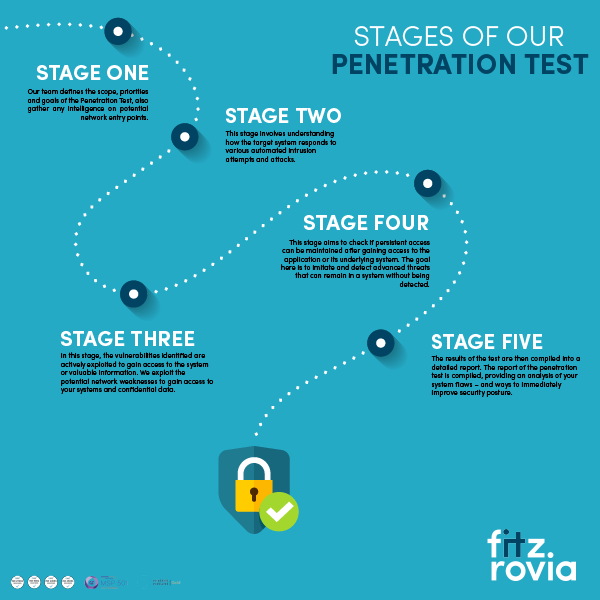
The five stages of a penetration test
1. Planning and Reconnaissance
Our team defines the scope, priorities and goals of the Penetration Test, also gather any intelligence on potential network entry points.
2. Scanning
This stage involves understanding how the target system responds to various automated intrusion attempts and attacks.
3. Gaining Access and/or Exploitation
In this stage, the vulnerabilities identified are actively exploited to gain access to the system or valuable information. We exploit the potential network weaknesses to gain access to your systems and confidential data.
4. Maintaining Access
This stage aims to check if persistent access can be maintained after gaining access to the application or its underlying system. The goal here is to imitate and detect advanced threats that can remain in a system without being detected.
5. Analysis and Reporting
The results of the test are then compiled into a detailed report. The penetration test report is compiled, providing an analysis of your system flaws – and ways to immediately improve security posture.
frequently asked questions
What are the potential risks of a data breach?
Some of the potential risks following a data breach may include:
- Financial risk: Companies found to be noncompliant in-line with GDPR, will be fined €20 million (£17.5 million), or 4% of their global annual turnover, whichever is greater.
- Reputational risk: Following a data breach, a business may struggle to regain trust with clients.
- Personal risk: Data breaches are more likely to cause greater financial and reputational damage if sensitive personal data has been infiltrated. Home addresses, credit card details, names and ages, are often used for fraudulent activities permanently disrupting a victim’s life.
How often should I be testing my systems?
Fitzrovia IT advises that you pen test quarterly. However, if your IT infrastructure or software is updated frequently, is complicated or if you could be a popular target for an attack, (i.e. an online bank, retailer or similar business), then testing should be carried out monthly.

Why use Fitzrovia It?
Penetration Testing services from Fitzrovia IT will uncover any potential security flaws in your business's network. We conduct internal/external infrastructure, Wi-Fi, API, and Web Application tests to identify vulnerabilities. Regular tests will safeguard your business from the numerous financial and reputational ramifications that you could face in the event of a cyber-attack.
Using both automated and manual technologies, every penetration test we carry out will identify and exploit issues that could potentially compromise network assets. This gives you a complete understanding of your network weaknesses as well as a priorities action list for dealing with them.
With concern mounting for organisations of all sizes, Fitzrovia IT advises that businesses conduct regular penetration tests. Security flaws exist in software, hardware, and configurations irrespective of the size of the organisation. One of our core beliefs is that we believe in prevention over intervention, so make sure you are best prepared to not fall foul of a breach or fine.
ENQUIRE ABOUT PENETRATION TESTING
Fill out the form below, and we'll contact you to discuss your requirements.








